Exploring simulated robotics and its data capture with Scurid Edge Agent to enhance security in Digital Twin Computing - Part-I



Overview
Digital twin computing is a paradigm that enables the creation of a digital replica of physical assets, processes, and systems. Not a new concept, digital twin computing has been around for a while, but it has gained significant traction in recent years due to the rise of the Internet of Things (IoT) and Industry 4.0.
Using the data collected from the physical asset, the digital twins help:
- Simulate,
- Predict, and
- Optimize the performance of the physical asset.
This can be used to improve:
- Efficiency,
- Reliability,
- Safety of the physical asset
- Reduce cost of maintenance and operation.
Several companies are already delivering digital twin computing solutions for various industries.
AWS IoT Twin Maker
"AWS IoT TwinMaker makes it easier for developers to create digital twins of real-world systems such as buildings, factories, industrial equipment, and production lines." see AWS IoT Twin Maker
Classifying Digital Twins in
- Component Twin, representing a single component or device
- System Twin, representing a collection of components or devices
- Process Twin, representing a process or workflow
- Asset Twin, representing a physical asset such as a building, vehicle, or machine
NTT DTC Digital Twin Computing
"NTT's Digital Twins Computing (DTC) goes one step forward: it enables digital twins to interact among themselves, freely recombining theme to perform more precise simulations of the real world." see NTT DTC
- First, DTC makes it possible to create digital twins combined with data from environment sensors.
- Then it builds precise copies of real-world, complex systems such as cities, traffic, infrastructures and even human bodies.
- Finally, it makes it possible to conduct highly precise experiments and trials to better plan the future and correct or mitigate damage.
Challenges in Digital Twin Computing
These are some very exciting developments in the field of digital twin computing. However, there are some complex challenges that need to be addressed to make digital twin computing more secure and reliable. To name a few:
- Data privacy and security,
- Integrity and Authenticity of data,
- Scalability of Security Measures,
- Access control
Common attacks:
NOTE: not an exhaustive list
- Man-in-the-middle: Demonstrated in this case study attackers can intercept the communication between the digital twin and the physical asset and manipulate the data. See MITM
- Identity Spoofing: Today's common digital identity frameworks for the devices use traditional PKI based identity or a simple username/password based identity. Attackers may impersonate legitimate users or devices to gain access to the digital twin system, allowing them to manipulate data or disrupt operations.
These traditional identity frameworks gravely lacks the ability to add device context to the identity, which is crucial for maintaining strong binding between the device and its identity.
We wanted to explore how Scurid platform could help enhance the security of digital twin computing
To give you a high level overview, how digital computing architecture could look like
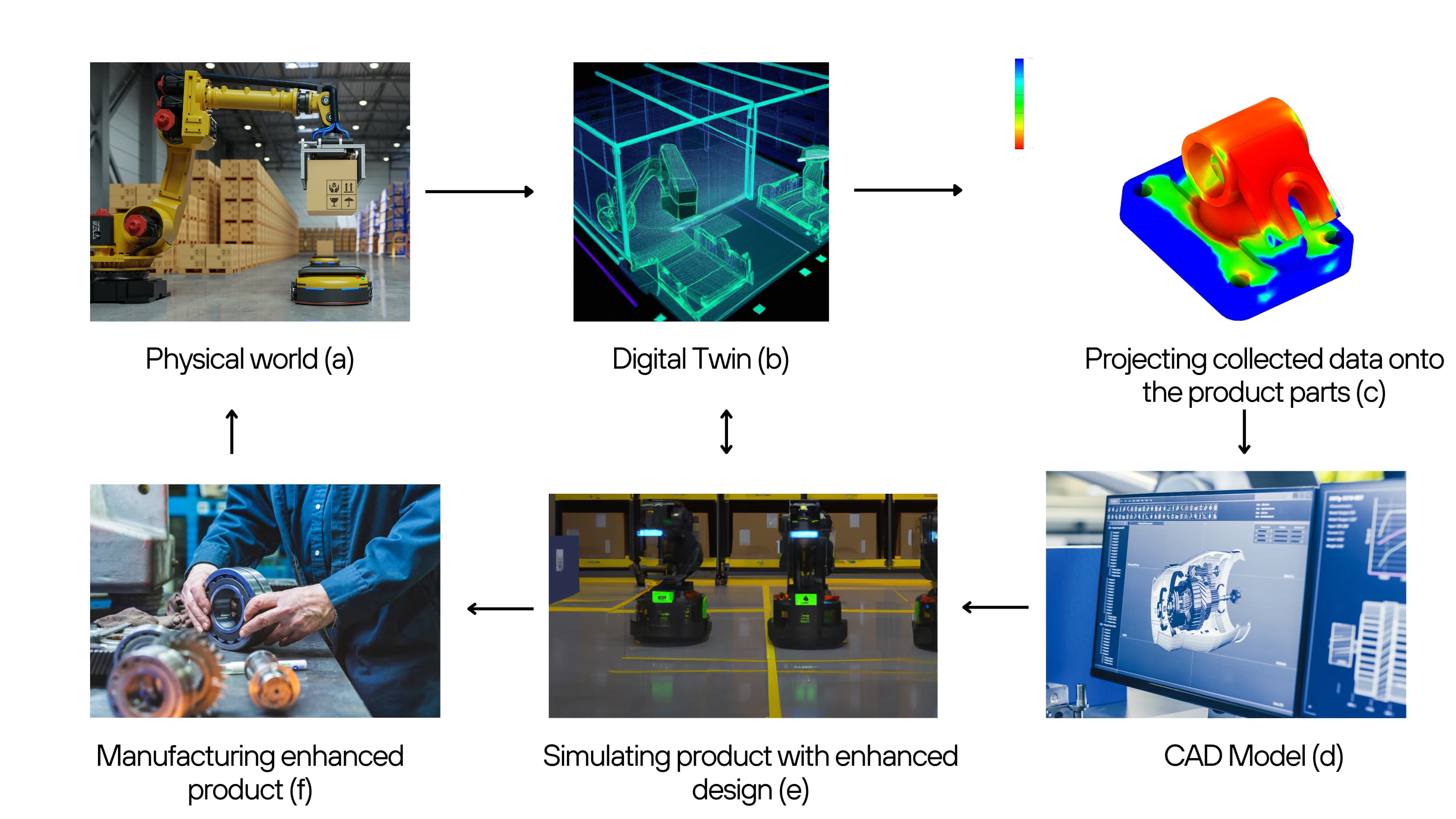
In the Figure-1, we have a digital twin computing architecture that consists of the following components:
- Physical world, consisting of physical asset which could be one or more robot in this case let's say robots operating in a warehouse.
- Digital Twin, which is a digital replica of the physical asset.
- Projecting collected data onto the product parts to learn and predict the behavior of the physical asset.
- CAD Model refinement to optimize the performance of the physical asset.
- Running simulation with enhanced CAD model to predict the performance of the physical asset.
- Manufacturing the optimized parts and replacing the old parts with the new ones.
Here we have a circular flow of data from the physical asset to the digital twin and back to the physical asset.
Now, let's put this into a simpler and more concrete example with scope on simulated digital twins.
Simulated digital twin of robots in a warehouse
A robot is a programmable device capable of carrying a complex series of actions, based on the knowledge of its environment. Each robot comprises a set of sensors and actuators; where sensors help collect data from the environment and actuators take actions in the physical space. Data integrity and authentication are always a challenge in robotics, as the robots most of the time operate in unmonitored environments which makes them vulnerable to adversarial attacks. The challenge gets more complicated in multi-robot settings where robots from different organisations need to communicate with each other. An adversary can monitor the network over the time to observe communication patterns and attempt to dereference a robot’s identity based on the data exchange and communication patterns.
Creating task for the robots
A group of independent robots (n=3) are on a mission to find out certain rare traces.
- The trace is defined as a colour. Each robot is equipped with a sensor that reads the colour of the ground. Accordingly, the robot also calculate the coordinates of its position.
- The simulation starts with the robots randomly exploring the environment, sensing and sending trace information to the server.
- The robot runs a Scurid Edge Agent that signs the sensor value along with other information and sends it to the Scurid Server.
How and what are we using to simulate the entire scenario
- Scurid Edge Agent, running on the robots to deliver unique distributed digital identity, collecting and signing the sensor data
- Scurid Server, handling connections from the robots and storing the data
- Scurid App, to manage and monitor the agents running on the robots
- Argos Simulator, a multi-physics robot simulator
Check out this video to see how the robots are exploring the environment and sending the data to the server.
What key factors are in play and how Scurid is helping in this Scenario
- Managing the robot identity, so it can be globally identified and authenticated across the ecosystem.
- Managing the secure connection to the Scurid server, so you don't have to worry about it.
- Setting up and managing the data stream for pushing values to the Server.
- Managing the data signing before sending it to the Scurid server, so you can verify the data integrity and authenticity
- Handling the sensor data from the robot software in the desired data format
Result
Even in the simulated environment, we were able to demonstrate how Scurid can help in not only delivering the digital identities to these simulated robots but also enable verifiable data stream from the robots to the server and finally to the digital twin.
- Scurid generates "device-context-aware" identities that are harder to spoof, copy or manipulate.
- Scurid Edge Agent signs the sensor data before sending it to the server, ensuring the data integrity and authenticity.
Addressing key attack vectors in the digital twin computing space.
What's next
In the next blog posts we will be unfolding the above-mentioned steps used to simulate the experiment. We will be mainly discussing the code for robot controller and the middleware used to enable robots to exchange data with the Scurid platform.
Mentioned in this article
Edge Agent
Empower your devices with the Scurid Edge Agent a fusion of robust digital identity, trusted data exchange, and sleek efficiency. Crafted for the discerning IoT architect, it is the future of device autonomy and security.
Server
A server application designed to be deployed on-premise, private cloud or managed as a service by Scurid.
App
A unified cross platform desktop native app to manage fleets of devices in your IIoT ecosystem. Minimizing programming effort to help bring easier access to data verification and trust.
An established platform for your IoT devices and data. Ready for production.
With Scurid’s easy-to-use API-based platform for hardware, sensors, and applications we want to enable the adoption of secure autonomous systems. Scurid is already trusted in production, helping our users achieve a faster and safer go-to-market.