Device Identity Management and trusted data exchange with Scurid for Hardware as a Service (HaaS) business model.


Introduction
Scurid is an IIoT device identity and access management (IAM) platform that augments device identities with interoperability and data management features. Our IAM platform also makes it extremely easy to connect devices, IoT platforms, databases, and applications. Our objective is to simplify the adoption of secure digital identities and data trustworthiness for IoT devices. With Scurid we want to enable our clients to introduce secure autonomous systems in their applications. With a deployment base of more than 1000 devices, Scurid is production-ready and is already enabling our customers to go to market faster and safer.
The Importance of Secure Digital Identity in IoT Systems
In the rapidly evolving world of technology, drones have emerged as powerful tools for various applications. From aerial photography to package delivery, drones have the potential to revolutionize industries. Among the new business models being applied to drones, there is Drone-as-a-Service, where drones have a multitude of users. However, managing drone identities and ensuring the trustworthiness of data can be challenging. The challenge is in implementing IoT authentication and authorization routines in your device infrastructure. In this note, we will explore how Scurid can help manage drone identities across multiple third-party systems while delivering also trusted data to a multitude of stakeholders (such as users, service providers, or Government entities).
As IoT usage continues to grow, exposing a wider attack surface for malicious actors, the need for secure digital identities becomes increasingly crucial. Moreover, onboarding hundreds or thousands of devices becomes challenging, leaving space for human mistakes in hardware configuration. Finally, IoT devices, such as drones, generate vast amounts of data that must be protected.
Scurid offers a solution
Scurid offers an identity SDK and an embedded device agent that makes a developer’s life easy when dealing with device interoperability, and intermittent connection handling while maintaining authentication on the edge, allowing you to integrate various data sources such as sensors or even other software applications running on your devices. You can use our APIs for easy integration of authentication and to fingerprint the data. You can, for instance, certify the trustworthiness of the device-generated data. Freedom from fixed passwords or API Keys.
Use Case: Managing Drone Identities and Delivering Trusted Data
To understand how Scurid can help manage drone identities and deliver trusted data, let’s explore a specific use case involving three types of user profiles: a drone manufacturer (Drones Inc.), a drone rental company for package delivery (FastDelivery Inc.), and the end customer tracking the delivery (Customer).
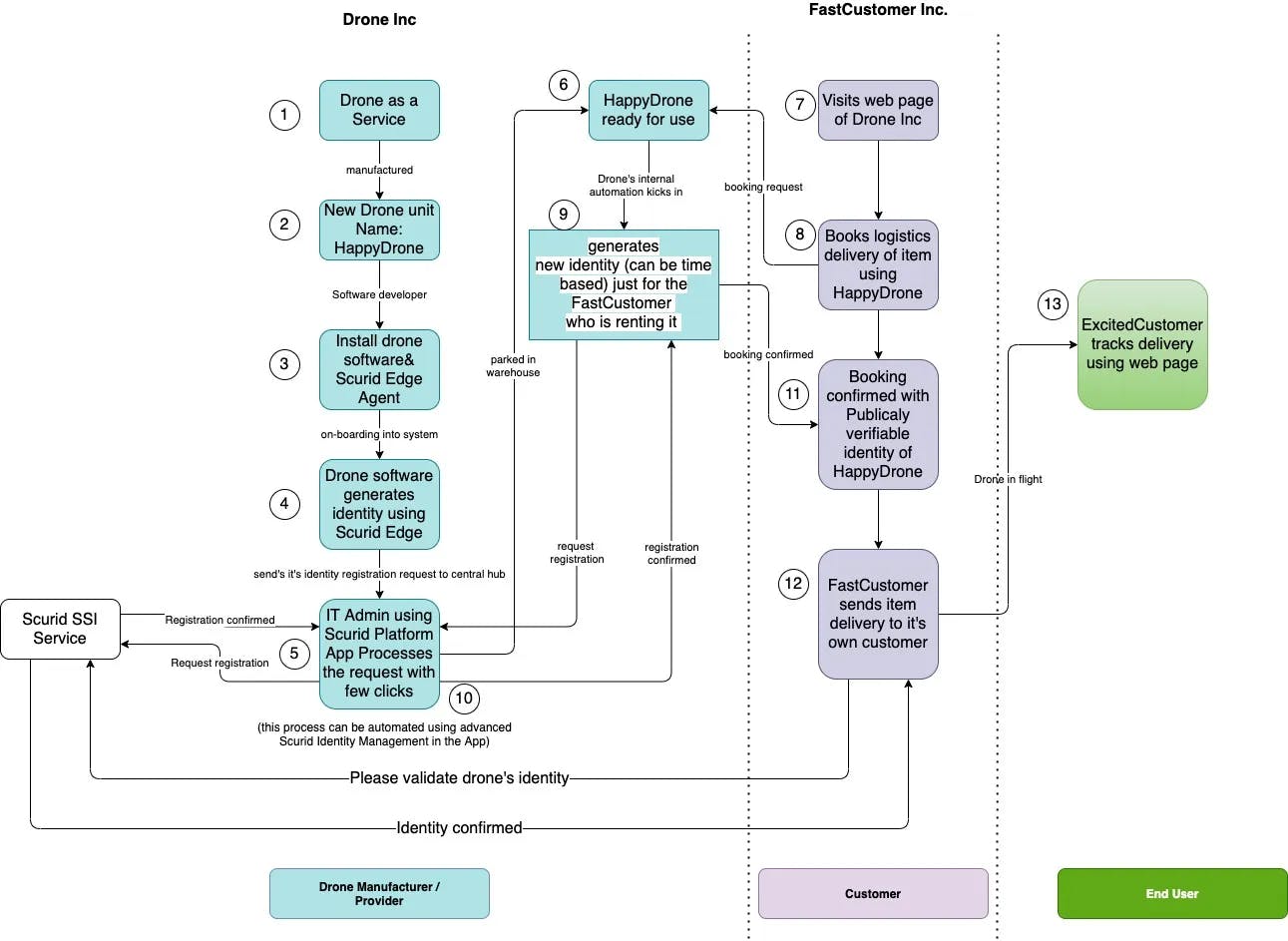
- Drones Inc. manufactures the drones and installs its own IoT software and Scurid Edge Agent on the newly manufactured drone.
- The drone is switched on and onboarded into the internal system of Drones Inc., which includes an IoT platform, analytics platform, and inventory management platform.
- Scurid Edge Agent generates a distributed digital identity for the drone and sends a request to the Scurid Server installed at Drones Inc.’s servers.
- An IT administrator from Drones Inc. approves the new drone’s identity in the Scurid Server, triggering automatic onboarding with the three systems mentioned above.
- The drone now has an internal identity ready and onboarded in all required systems, making it available for booking.
- Drones Inc. makes the device available for booking and visible on its web portal.
- FastDelivery Inc. receives an order from the Excited Customer for goods delivery. Their SaaS platform automatically calls an API from Drone Inc.’s available inventory to check for the list of immediately available drones.
- A booking call is made to the first available drone that can handle the weight and delivery duration. This API call triggers a time-bound identity on the device via Scurid Edge Agent.
- The automated approval process onboards this identity into the Drone Inc. system to reference and track the drone assigned for work to FastDelivery Inc.
- A new identity is created for the specific task, hiding the internal identity used by Drones Inc. The drone now has an external identity for use with the FastCustomer Inc. system until the work is done, at which point the identity is automatically revoked.
- FastCustomer Inc.’s internal SaaS services receive confirmation of having acquired an available drone for delivering the goods.
- The drone takes off, lands at the FastCustomer warehouse, picks up the order, and starts the delivery service to the Excited Customer.
- The Excited Customer can track the status of their order on their phone using an app provided by FastCustomer Inc.
- The app also provides a mechanism for verifying the data that the drone is sending to all stakeholders, ensuring the trustworthiness of the delivered goods’ metadata.
Salient Features we help enable
API-first approach
We provide a simplified set of APIs to help developers quickly create globally unique and distributed digital identities on their IoT devices. Our Edge Agent framework, as part of the core functionality, enables you to have your devices generate identity and reach out for identity workflow actions from Scurid API.
Fast identity creation
A built-in data tamper evident mechanisms that allow the edge device identity to offer trust in the data, from source ( edge) to anywhere in your system, including external partners. Device onboarding doesn’t require human interaction, and we offer capabilities to auto-approve an identity when coming from trusted Agents, further simplifying the individual identity workflow.
Encryption and fingerprinting
Scurid Edge Agent seamlessly handles encryption, to prevent unwanted access to the private keys created on the device. The Agent or the Device identity’s private key can be used to fingerprint a variety of data generated by the device. The fingerprinting enables you to verify the data’s trustworthiness even weeks, months, or years after the collection.
Built-in data authenticity
Scurid Edge Agent creates a verifiable signature on data collected from the device, which gets sent and stored along with the data. Data consumers can use this signature to verify if the received data came from the specified digital identity of the device. In the Drone-as-a-Service example use-case, Scurid establishes a “chain of custody”: trustworthy metadata allows for tracking and documenting the movement of goods from the sender to the recipient, including any intermediate steps or transfers. This is vital for legal, regulatory, or insurance purposes, as it provides a clear record of responsibility and accountability in case of disputes, damages, or loss.
Security and privacy of all the users
In the Drone-as-a-Service example use case, trustworthy metadata helps protect the security and privacy of both the sender and the recipient of the delivered packages. By accurately documenting relevant information, such as the sender’s and recipient’s identities, addresses, or transaction details, it minimizes the risk of identity theft, unauthorized access, or misuse of personal information. It also facilitates effective communication between the parties involved in the delivery process.
Context-aware identities
For clients supporting Hardware as a Service business models with multiple users, Scurid enables to have multiple identities on the same hardware, with no need to reuse the same identities across multiple users. The same context-aware identities allow you to manage and transfer different configurations bound to a specific identity, even on the same device.
Revoking unused device identity automatically
This feature is crucial for several reasons:
- It enhances security by reducing the attack surface and minimizing the risk of unauthorized access to sensitive systems. Unused device identities can become targets for malicious actors seeking to exploit vulnerabilities.
- It helps in managing device inventory and maintaining accurate records, enabling efficient troubleshooting and maintenance processes.
- Revoking unused device identities ensures compliance with industry regulations and standards, promoting a robust and secure IoT ecosystem.
Cheaper development and maintenance
Scurid users save the effort of 2–3 developers and administrators that need to deal with device onboarding. Countless hours are saved in data auditing, especially for projects in highly regulated industries. This is possible thanks to Scurid’s standardization and scalability efforts in building predictable API endpoints, which is fundamental for system integrators and their software developers. You can start with just a few devices, and scale to thousands of them with the same identity layer.
Avoiding vendor lock-ins
When customers want to remain agile, Scurid allows them to be vendor-independent. If they want to move from AWS to Azure, the identity piece of your applications will stay the same. And if you want to add other pieces of software (e.g. predictive maintenance), you can use exactly the same identities and identity orchestration mechanism. Scurid can also work both on-premise and in the cloud.
Conclusion
In conclusion, we offer a platform that simplifies and secures device interoperability. Without Scurid, developing and maintaining such a system would be time-consuming and expensive. We've saved our customers hundreds of thousands of dollars in manpower and data auditing costs. Additionally, through managing drone identities across multiple third-party systems, Scurid enhances the reliability and autonomy of devices, while at the same time protecting the privacy of the device end-users. With Scurid, the drone industry can optimize operations and provide end customers with a seamless and trustworthy experience.
Mentioned in this article
Related Posts
Device Identity Management and trusted data exchange with Scurid for Hardware as a Service (HaaS) business model.
Supercharge your Digital Twin’s data security with Scurid’s new release.
An established platform for your IoT devices and data. Ready for production.
With Scurid’s easy-to-use API-based platform for hardware, sensors, and applications we want to enable the adoption of secure autonomous systems. Scurid is already trusted in production, helping our users achieve a faster and safer go-to-market.